substitution ciphers
Complete
Summary
Encryption and decryption
Key space and size
- the substitution table is the key
number of ways to arrange
objects without replacement
Concept
Substitution table, over an alphabet
substitution must be bijective
Known plaintext attack
- not secure
- given a sufficiently long ciphertext, the full substitution table can be found
Ciphertext only attack
- frequency analysis
- examining how frequently characters appear in the ciphertext and mapping them to their frequency in English
- quipquip and dcode.fr frequency analysis
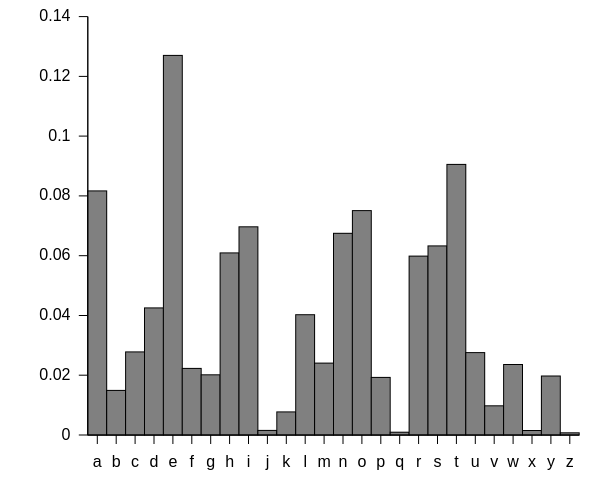
Application
Ceasar/shift cipher
ROT3 on Cyberchef, shift cipher’s only have
possible keys